Next: 7 File sharing Up: Maemo PC Connectivity Previous: 5 Internet sharing Contents
With Maemo PC Connectivity, it is possible to execute shell commands on another computer across network. That is, you can remotely execute shell commands on maemo device from your host PC and vice-versa. For that, you have to install maemo-pc-connectivity meta package on maemo device and host-pc-connectivity package on host PC (Linux, Windows and Mac OS). Next, it will be described how to use the remote shell tools available on Maemo PC Connectivity. To simplify, it is assumed that you already have a Usb network between maemo device and host PC.
Note: on host PC, you should type the commands bellow at terminal on Linux and Mac OS and at Cygwin shell on Windows.
Secure Shell (SSH) is a network protocol that allows data to be exchanged using a secure channel between two networked devices. It was designed as a replacement for Telnet and other insecure remote shells, which send information, notably passwords, in plain text, leaving them open for interception. With SSH, you can remotely execute programs on maemo device from your host PC and vice-versa. Next, it will be described the steps to access your maemo device from host PC.
ssh root@192.168.2.15
Here, root is the user name on 192.168.2.15 (network address of maemo device). If it is your first connection attempt to maemo device, you will be asked to verify the connection:
The authenticity of host 'host (192.168.2.15)' can't be established. RSA key fingerprint is ff:ff:ff:ff:ff:ff:ff:ff:ff:ff:ff:ff:ff:ff:ff:ff. Are you sure you want to continue connecting (yes/no)? yes Warning: Permanently added 'host,192.168.2.15' (RSA) to the list of known hosts.
ssh root@192.168.2.15's password:
Note: the root password is requested when you install openssh. maemo-pc-connectivity installs openssh if it is not installed yet. If you installed openssh before, the root password will not be requested on maemo-pc-connectivity installation.
BusyBox v1.6.1 (2007-09-27 18:08:59 EEST) Built-in shell (ash) Enter 'help' for a list of built-in commands. Nokia-Nxxx:~#
To avoid typing password every time, the remote machine needs to authorize the local machine identity. The process works on both direction, so the meaning of remote and machine will change. Here, the remote machine will be the maemo device and the local machine will be the host PC. It follows the needed steps:
# On host PC
$ ssh-keygen -t rsa
Generating public/private rsa key pair.
Enter file in which to save the key (/home/localuser/.ssh/id_rsa):
Created directory '/home/localuser/.ssh'.
Enter passphrase (empty for no passphrase): <hit enter>
Enter same passphrase again: <hit enter>
Your identification has been saved in /home/localuser/.ssh/id_rsa.
Your public key has been saved in /home/hostuser/.ssh/id_rsa.pub.
The key fingerprint is: f:ff:ff:ff:ff:ff:ff:ff:ff:ff:ff:ff:ff:ff:ff:ff
# On host PC
$ scp ~/.ssh/id_rsa.pub remote_username@remote_ip_address:/tmp
remote_username@remote_ip_address's password:
$ ssh remote_username@remote_ip_address
remote_username@remote_ip_address's password:
# On maemo device
$ mkdir -p ~/.ssh
$ cat /tmp/id_rsa.pub >> ~/.ssh/authorized_keys
# On maemo device $ chmod 600 ~/.ssh/authorized_keys
You should apply the steps above for every local and remote user combination. For example: if you want to connect to root and user accounts on maemo device from root account on host PC, you need to generate a key pair for root account on host PC and copy the public key to database of authorized keys (root and user accounts) on maemo device
On host-pc-connectivity package, it is provided a tool named ssh-key-exchange that exchanges SSH public keys automatically. Thus, SSH will not ask password every time. For that, you should execute the following command:
ssh-key-exchange -l local_ip_address -r remote_ip_address -u remote_username
After exchanging keys, the next SSH connections will not require password.
Scratchbox Remote Shell (SBRSH) is a remote shell solution such as SSH. It allows you to execute programs on maemo device from host PC, but using the host PC file system, instead of maemo device file system. The following steps show how SBRSH works:
It follows the steps to configure SBRSH through Maemo PC Connectivity:
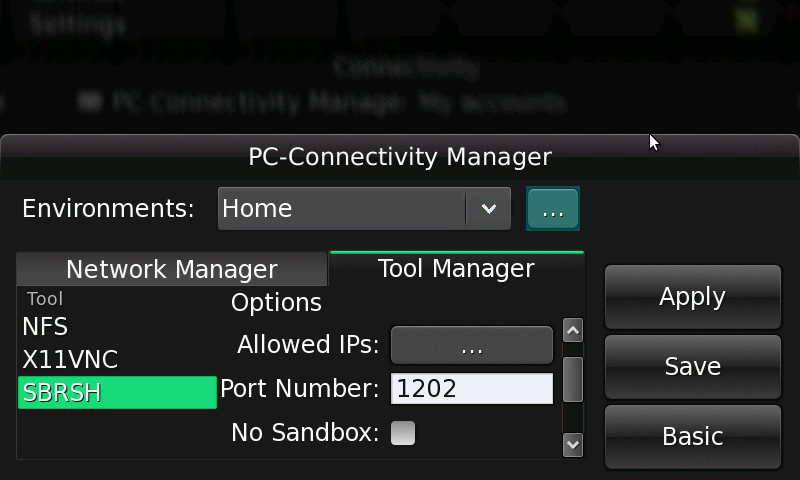
Otherwise, you can setup SBRSH manually. For that, you have to edit the following configuration files:
DEBUG: enable debug logging to /var/log/sbrshd.log file or to the file defined at DEBUG_FILE. This can be useful if you are having trouble while connecting. Also, you can execute sbrshd -enable-debug or sbrshd -disable-debug to toggle debug option dynamically.
NO_SANDBOX: this option became deprecated since version sbrshd-7.6maemo3, once SBRSH client can switch from SANDBOX and NO_SANDBOX by passing -s or -n option, respectively. It follows the meaning of SANBOX and NO_SANDBOX:
EXPIRATION: defines in minutes how long sbrshd will wait before unmount shares. Since the typical sandboxed usage of sbrshd will cause a significant delay the first time you connect (because most of the shared libraries and shell related binaries from the host PC must be passed over the network), you will usually set a long expiration time.
By default, the installation of maemo-pc-connectivity meta package has configured these options to no debugging, sandboxed enabled, and 15 minute expiration.
If you changed this file, you should restart the SBRSH daemon to get the configuration working:
# /etc/init.d/sbrsh restart
Note: SBRSH does not use a secure protocol, so be judicious in granting access!
In this example, SSH will be used to configure SBRSH client. So, you can use ssh-key-exchange as described in section 6.1 to avoid SSH requiring password every time.
In order to use SBRSH client, you need a configuration file to select the targets of the devices and which file systems they export from host. By default, the file used is /.sbrsh, but you may override it by using the following command sbrsh -c <file_name>. The first target defined on configuration file is used by default, but you may override it by using the following command sbrsh -t <target_name>. Next, it will be explained the SBRSH configuration file format
You need to edit SBRSH configuration file to setup which host PC folders will be mounted on maemo device. The configuration file format is:
# <target_name> <host_name>[:<port>] # nfs|bind|sshfs <host_filesystem> <target_mountpoint> [<options>] # ...
A blank line separates entries. Since SBRSH client 7.6, a hash mark ``#'' denotes commented lines.
As you can see, SBRSH uses SSHFS or NFS in background to mount host PC file system on maemo device. For new users, it is recommended SSHFS since you just need to edit SBRSH configuration file. With NFS, you need to edit NFS configuration as well. Also, the mounts should appear in order of increasing depth. For example: the root (/) must be mounted first, then the folders inside it (/home) and so on.
The bind lines overrides portions of of the target file system with the host file system. This is essential for file systems which contain maemo device specific files and/or folders. For instance: /tmp, /var, /sys, /dev, /proc, etc. See more details on example below.
It is recommended to unmount SBRSH (sbrsh [-c <file_name> -t <target_name>] -umount) before editing SBRSH configuration file. SBRSH commands read the current configuration file. If you first changed the configuration file, SBRSH will not remember the old configuration. Thus, SBRSH will not unmount the old configuration correctly.
It follows a example of SBRSH configuration file:
User name: you
Target: DIABLO_ARMEL
sshfs-target 192.168.2.15 ssh you @192.168.2.14:/scratchbox/users/you /targets/DIABLO_ARMEL/ / rw,nonempty,allow_other ssh you @192.168.2.14:/scratchbox/users/you /home/you / /home/you rw,nonempty,allow_other bind /tmp /tmp bind /dev /dev bind /dev/pts /dev/pts bind /proc /proc bind /sys /sys bind /var /var
In CPU transparency mode, the SBRSH configuration file is determined by SDK target location and the first target is used by default. You can follow the next steps to use SBRSH in CPU transparency mode on scratchbox:
cd /scratchbox/devkits/cputransp/bin/ mv sbrsh sbrsh.old cp <pc_connectivity_sbrsh_client_binary> sbrsh
SBOX_CPUTRANSPARENCY_METHOD=/scratchbox/devkits/cputransp/bin/sbrsh
You can also do this by creating a new target or by editing your current one through sb-menu command.
You can export SBOX_CPUTRANSPARENCY_EXTRA_ARGS variable to pass the additional parameters to new SBRSH client. If you want to turn off sandbox on server and want to use root user to execute the remote commands, you should execute the following line before SBRSH client:
export SBOX_CPUTRANSPARENCY_EXTRA_ARGS="-n -r 0,0,root"
If you changed SSH keys with root user on maemo device, you need to specify this on command line. Run the following command on host PC to see if the mount works:
$ sbrsh -r 0,0,root ls /
bin cdrom etc home lib mnt proc sbin sys usr
boot dev floppy initrd media opt root srv tmp var
Also, you can use -s or -n option to turn on/off sandbox mode on server, respectively:
$ sbrsh -n -r 0,0,root ls /
bin cdrom etc home lib mnt proc sbin sys usr
boot dev floppy initrd media opt root srv tmp var
$ sbrsh -s -r 0,0,root ls /
bin cdrom etc home lib mnt proc sbin sys usr
boot dev floppy initrd media opt root srv tmp var
You can get some errors while using SBRSH. Next, it will be described some of them:
$ sbrsh /bin/sh sbrsh: authentication failed
It means that you forgot to add the IP address of your host PC on /etc/sbrsh.conf file of your maemo device.
$ sbrsh /bin/sh sbrsh server: read: Connection reset by peer sbrsh server: Can't mount to point: /var/sbrshd/you@192.168.2.14/sshfs-target/
It happens because you do not have the same user on both machines (maemo device and host PC). Use the option -r to specify the user you will use to run the command on maemo device. For example: "-r 0,0,root". Also, be sure your SSH keys have been successfully exchanged between your user (host PC) and the root user of your maemo device. You can test trying SSH in both directions. No password should be required.
$ sbrsh /bin/sh sbrsh server: Can't execute command: /bin/sh (Permission denied)
This error is misleading. It usually means that you are missing a mount for the root directory on maemo device, when sandbox mode is enabled (the default). The error comes from chroot().
$ sbrsh my_app sbrsh server: Can't execute command: mu_app (No such file or directory)
Be sure that my_app path is visible from maemo device or specify a full path. For example: if you map ``/scratchbox/users/you/home/you /'' to ``/home/you /'', you should execute sbrsh /home/you /my_app instead.
$ sbrsh maemoapp maemoapp[2096]: GLIB ERROR ** default – file ... assertion failed: (result->osso) $ sbrsh maemoapp maemoapp[2096]: osso_initialize() failed
OSSO applications initialize the DBUS connection very early. So, DBUS problems are probably the cause. When launching OSSO applications, you must override the DBUS_SESSION_BUS_ADDRESS environment variable. The DBUS_SESSION_BUS_ADDRESS value of your host system is probably completely incorrect, since /tmp is bind-mounted to the target. Try the following command instead:
$ DBUS_SESSION_BUS_ADDRESS=unix:path=/tmp/session_bus_socket sbrsh maemoapp
Walter 2009-12-21